Do you remember when you were in school and the teacher would give each student a worksheet to “spot the difference” between two side-by-side detailed scenes? You would look carefully at each of the two images, trying to spot subtle details, such as an extra button on a shirt or a missing shoe on a person. Maybe it was the number of petals on a daisy or a cone of ice cream missing the cherry on top. The directions would indicate there would be six differences, but try as hard as you did, (and even when you asked a classmate for help) you could still only find four or five differences, and were convinced there was never a sixth.
Unnerving!
Today, the business-equivalent of spot-the-difference comes by way of email phishing.
Phishing is the attempt to obtain sensitive information (including your identifying information) such as credit card numbers or passwords to gain access into your electronic records or steal your identity.
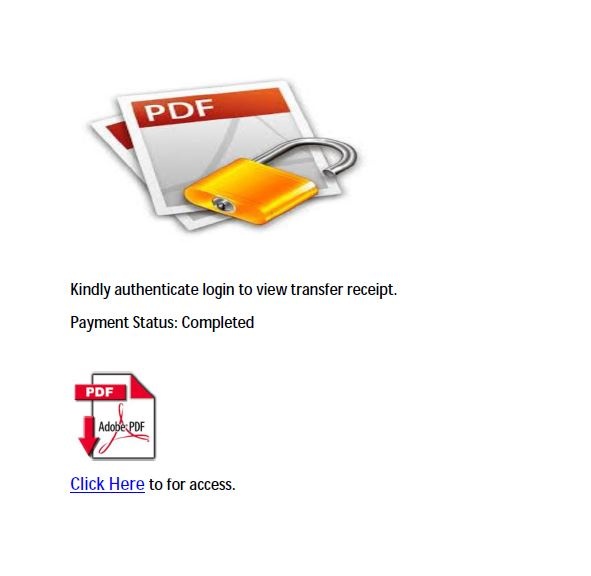
Can you spot which of these images is the imposter? 
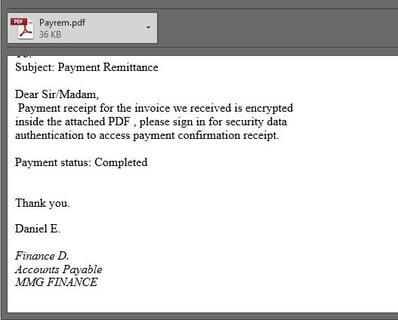
If you said the one on the top, you are correct.
If you said the one on the bottom, you are also correct.
Two of the more recent phishing scams target unsuspecting folks such as you and me through email. Not only during tax season, but also throughout the year, scammers are becoming more and more savvy both in their visual and written attempts to trap consumers. As companies are working to stay ahead of thieves with data security and multiple layers of password protection, it is no wonder many consumers are feeling confused and vulnerable. So, what can you do to avoid unknowingly falling into a phishing scheme?
Read more articles about IT security on Mike Jaworske's blog page
- Communicate with the company you are dealing with and confirm by phone their method of doing business. If you receive a communication by email asking for your sensitive information or for you to click on a link that takes you to a website asking you to enter your personal information, be wary. Knowing what you should be expecting from those with whom you do business and how they will be communicating with you will help you stay alert to bogus mail and false documents.
- Don’t click! Oftentimes, we click on a link trusting its navigation and, while it looks authentic, like it’s from a governmental entity or “official” agency, it is a bogus site. Spyware, malware, or other Trojans can easily infect your system(s) and wreak designed havoc.
- If you didn’t initiate the contact….don’t go there. Whether “there” means opening a document, visiting a website, or filling out a form with information as simple as your name and email address; thieves will begin with the basics and work for more over time.
If you are a business leader seeking advice to help your company improve its IT infrastructure to better serve your clients or, if you are an individual with questions about IT security or tax return identity theft, contact me at mjaworske@zinnerco.com or any of our professionals at 216.831.0733. We’re happy to start theconversation and ready to help direct you to the tools and resources you need to reduce the risk of identity and document theft.